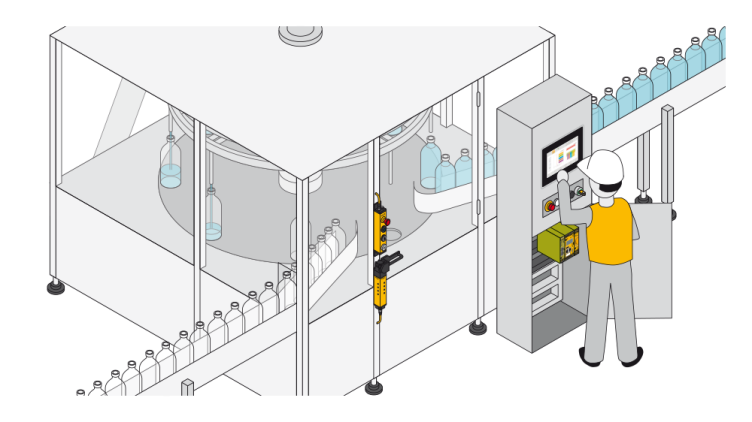
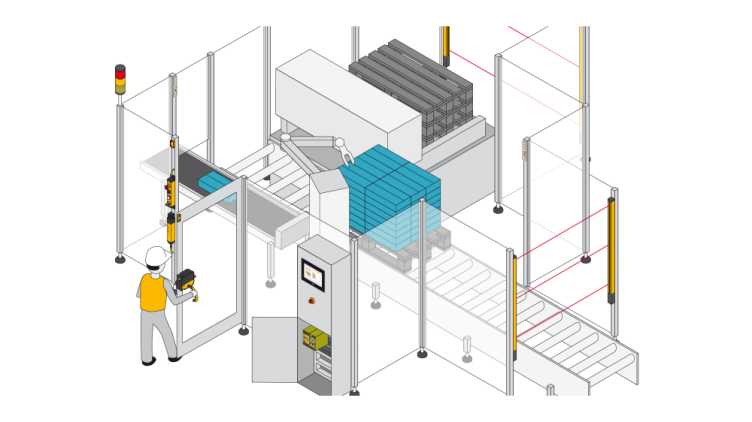
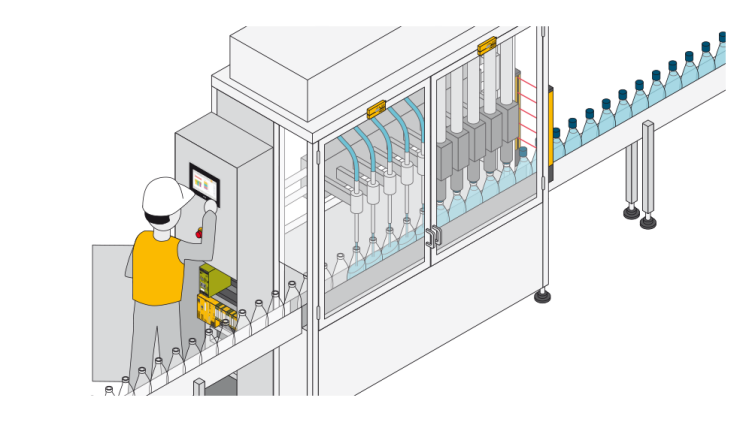
With our “Identification and Access Management” portfolio, we offer you a comprehensive range of products, solutions and software for the implementation of both Safety and Security tasks.
Below you'll discover more about potential applications, from simple authentication to complex access permissions, and access management through to safe operating mode selection, maintenance safeguarding and safeguarding of data and networks. Experience Safety and Security in one system!